An introduction to CYRIN features, as well as an introduction to the Linux Terminal, Windows PowerShell, and shell commands.
Expected Duration
1 hour, self-paced. Pause and continue at any time.
1 CPE awarded on successful completion.


Unlike other platforms, the Cyber Skills Cyber Range is engineered to provide superior training and education in three ways:
An introduction to CYRIN features, as well as an introduction to the Linux Terminal, Windows PowerShell, and shell commands.
1 hour, self-paced. Pause and continue at any time.
1 CPE awarded on successful completion.
Students will learn how to configure an Intrusion Detection System (IDS) to examine traffic to/from a firewall. The popular Snort® IDS will be used in this exercise. The exercise will include both harmless background traffic and potentially-malicious traffic to be detected by Snort.
Basic networking concepts (TCP/IP, DNS, etc.) and familiarity with the Unix/Linux command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Students will learn how to deploy, configure and customize a Zeek Network Intrusion Detection System (NIDS). They will customize Zeek to generate enterprise specific logs and to send email notifications of events of interest. They will also create a simple Zeek plugin, using the Zeek scripting language, to detect and block brute force ssh login attempts.
Basic networking concepts (TCP/IP, DNS, etc.) and familiarity with the Unix/Linux command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Students will configure a network firewall using the VyOS router appliance, which mimics physical router hardware. The exercise will include both ingress and egress filtering, stateful packet inspection, and best practices. Students will set up a partitioned network and a DMZ area to isolate specific enterprise services, such as an e-mail server. Evaluation will include network probes from both inside and outside the firewall to ensure proper rules are configured.
Basic network routing concepts (firewalls, subnets, etc.) as well as basic networking concepts (TCP/IP, DNS, etc.). Students must also be comfortable working in command-line environments.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Students will configure a network firewall using the standard Linux IPtables module. The exercise will include both ingress and egress filtering, stateful packet inspection, and best practices. More advanced techniques such as port knocking will also be introduced. Evaluation will include network probes from both inside and outside the firewall to ensure proper rules are configured.
Basic network routing concepts (firewalls, subnets, etc.) as well as basic networking concepts (TCP/IP, DNS, etc.). Students should also be comfortable with the Linux/Unix command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Students will learn to secure and configure the widely used, open-source pfSense firewall. They will learn to create firewall rules, the order in which rules are applied, how pfSense aliases can be used to simplify the pfSense rule set, and how to secure pfSense itself. They will also learn to view statistics and logs collected by pfSense.
Basic network routing concepts (firewalls, subnets, etc.) as well as basic networking concepts (TCP/IP, DNS, etc.). Students should also be comfortable with the Linux/Unix command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Students will learn to configure and set up an OpenVPN server. OpenVPN is an open-source Virtual Private Network (VPN) solution. VPNs extend a private network over a public network, allowing users to send and receive data the public networks as if they are directly connected to the private network.
Students will learn to set up a Certificate Authority to create the keys and certificates needed to (1) authenticate users (VPN clients) and the VPN server and, (2) encrypt communication between the two. They will also learn how to revoke client certificates when needed.
Basic knowledge of public key infrastructures and certificates, and familiarity with the Unix/Linux command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Hackers shouldn’t be able to explore your internal network. To make sure they do not, you need to learn about split horizon DNS configuration. And it might help to know something about BIND, probably the most used DNS software on the internet.
In this lab, students will configure a split-horizon DNS infrastructure that consists of two DNS servers: An External DNS server and an Internal DNS server. The External DNS lives in the organization's DMZ network; it is used by external hosts to resolve names of servers in the DMZ. The Internal DNS lives in the organization's internal network and is reachable only by hosts on the internal network. It resolves names of hosts on the internal network.
The lab uses BIND, the most popular DNS server in use today.
Basic network routing concepts (firewalls, subnets, etc.) as well as basic networking concepts (TCP/IP, DNS, etc.). Students should also be comfortable with the Unix/Linux command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

In this exercise students must configure the firewalls and routers of an enterprise network in accordance with the security policies of the organization. The computers and network devices in the network have been physically connected but the firewalls and routers have not been configured. You must configure these firewalls and routers to implement policies related to how traffic to/from the Internet and traffic between the different subnets is handled. This exercise is brought to you by the Rochester Institute of Technology-Global Cybersecurity Institute.
This exercise uses pfSense, an open-source firewall and router that is used by thousands of enterprises and officially supported by Netgate. Students must be familiar with the pfSense console and web interfaces. Those not familiar with pfSense are encouraged to complete the CYRIN Firewall Configuration with pfSense lab before attempting this exercise.
Basic networking concepts including IP routing, Network Address Translation (NAT), basics of network firewalls, and familiarity with pfSense.
If you are not familiar with pfSense and its configuration, complete the CYRIN Firewall Configuration with pfSense lab before attempting this exercise.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Students learn to use the Windows Active Directory service to create and manage domain user accounts. They also learn to set up security policies and assign these policies to users and organizational units.
Familiarity with the Windows desktop.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Students learn the proper setup of the OpenSSH remote administration tool, including security-relevant settings. During the exercise, students will learn best practices such as host filtering, public-key or Kerberos authentication, and PAM integration.
Basic networking concepts (TCP/IP, DNS, etc.) and familiarity with the Unix/Linux command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Students learn how to configure and run the widely-used, free OSSEC Host Intrusion Detection System (HIDS). During the exercise, students will learn how to check for rootkits using OSSEC, how to verify file integrity, how to set up passive and active responses, and more. Host intrusion detection is critical to maintaining a secure system, and is required by HIPAA and PCI regulations, both of which OSSEC can help you meet.
Basic networking concepts (TCP/IP, DNS, etc.) and familiarity with the Unix/Linux command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Students will use tools such as nmap, unicornscan, and fping to identify systems on a local network, including both Unix and Windows targets. Students will identify the operating systems these systems are running, as well as the types of network services they are providing.
Basic networking concepts (TCP/IP, DNS, etc.) and familiarity with the Unix/Linux command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Students will use multiple tools to identify services, including software package and version information, running on unknown systems. Network services to be targeted will include those running on non-standard ports or behind firewall rules.
Basic networking concepts (TCP/IP, DNS, etc.) and familiarity with the Unix/Linux command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Students will build on the Service Identification I exercise to use service-specific information-gathering tools. Students will gather vendor, software, and version information, as well as any configuration information available remotely. Students will then use scripting tools to automate this process.
Basic networking concepts (TCP/IP, DNS, etc.) and familiarity with the Unix/Linux command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

This lab teaches students to setup and configure a central RSYSLOG server that will receive and store logs from FreeBSD, Linux and Windows clients.
Students will learn to configure log forwarding on the clients, and log rotation and filtering on the server. They will also learn to use Logwatch to analyze logs and fail2ban to automatically respond to suspicious activity found in the logs.
Basic networking concepts (TCP/IP, DNS, etc.) and familiarity with the Unix/Linux command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

In this lab the student will learn how to configure and securely run the Splunk Enterprise security information collection and analysis platform. The objective of the lab is to deploy multiple instances of Splunk data forwarders through a deployment server and analyze the logs received from the servers. The student will write custom scripts to generate logs, create both visual and textual reports, organize these reports into a single dashboard, and learn to recognize malicious activity.
Intermediate understanding of networking concepts and services (TCP/IP, SSH, etc.) and a basic understanding of shell scripting in bash (Linux) and PowerShell (Windows). Familiarity with the Linux and Windows environment, command line tools, and text editors (vi, vim, nano, or emacs) is also required.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Elastic Stack is a group of services designed to take data from almost any type of source and in almost any type of format, and to search, analyze and visualize that data in real time. In this lab, Elastic Stack will be used for log analytics. Students will learn to set up and run the Elasticsearch, Logstash and Kibana components of Elastic Stack. Multiple computers in a small network will forward their logs to a central server where they will be processed by Elastic Stack. Student will use Kibana to view logs, filter them and set up dashboards. Information in the logs will be used to identify and block an on-going attack.
Familiarity with the Unix/Linux command line, as well as SSH, sudo, and other common tools.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Students will gain experience with the widely-used open source Metasploit® framework and related tools for exploiting vulnerable software and insecure system configurations. The exercise leads students through the entire process, from scanning the network to getting remote shells and accessing sensitive information. By seeing the tools available to potential attackers, students will gain a greater appreciation for the need to keep software up-to-date and securely configured.
Basic networking concepts (TCP/IP, DNS, etc.) and familiarity with the Unix/Linux command line.
1 hour, self-paced. Pause and continue at any time.
1 CPE awarded on successful completion.

Students will use the free OpenVAS web tool suite to identify vulnerabilities in services available on an unknown network. The network will include several targets with known-vulnerable software versions and/or configurations.
Basic operating system security concepts, networking concepts (TCP/IP, DNS, etc.), and familiarity with the Unix/Linux command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Students will build on the results of labs in the Web Application Security Analysis and Network Monitoring categories by using the SPARTA network infrastructure penetration testing tool, a graphical application that automates many common vulnerability assessment tasks. Students will use SPARTA within a graphical Kali Linux environment, scanning multiple unknown target systems and exploring found weaknesses.
Basic web application knowledge (HTTP, URL parameters, etc.), networking concepts (TCP/IP, DNS, etc.), and familiarity with the Unix/Linux command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Students will learn how to set up a web server securely by configuring the commonly-used Apache HTTP Server® on a Linux system. Security options will be explored, including location/directory restrictions, permissions, authentication, and SSL configuration.
Basic web application knowledge (HTTP, URL parameters, etc.), networking concepts (TCP/IP, DNS, etc.), and familiarity with the Unix/Linux command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.
Students will build on the basic Apache configuration exercise to configure Secure Sockets Layer (SSL) encryption for the Apache HTTP Server®. Students will learn and implement best security practices and strong cryptography guarantees while avoiding vulnerabilities such as Heartbleed.
Basic web application knowledge (HTTP, URL parameters, etc.), networking concepts (TCP/IP, DNS, etc.), and familiarity with the Unix/Linux command line. The Secure Configuration of the Apache Web Server course is recommended before taking this course.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.
Students will learn about the LAMP (Linux, Apache, MySQL, PHP) stack and will deploy a LAMP stack running an application written in PHP. LAMP is one of the most common software stacks for many of the web's most popular applications. This lab is brought to you by the Rochester Institute of Technology Global Cybersecurity Institute.
Students will set up a LAMP stack to run WordPress, a PHP application. They will set up a MySQL database for use by the WordPress application, and will configure Apache to serve up the PHP pages for the application.
Students will learn just enough of the MySQL command line and of Apache configuration needed to deploy a LAMP stack. They can learn more about MySQL and Apache configuration in the labs An Introduction to MariaDB and MySQL, Secure Configuration of the Apache Web Server, and Secure SSL Configuration in Apache.
A very basic understanding of web applications and relational databases.
1.5 hours, self-paced. Pause and continue at any time.
1.5 CPEs awarded on successful completion.

Students will use the OWASP program’s ZAP tool suite from within Kali Linux to scan multiple web services and document vulnerabilities. Students will see ZAP in action on a vulnerable web site where entire database tables are available to potential attackers.
Basic web application knowledge (HTTP, URL parameters, etc.), networking concepts (TCP/IP, DNS, etc.), and familiarity with the Unix/Linux command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Students will use the Nikto tool to test web services over the network and document vulnerabilities. Students will then use network packet capture tools such as Wireshark to verify their understanding of the vulnerabilities and testing procedures.
Basic web application knowledge (HTTP, URL parameters, etc.), networking concepts (TCP/IP, DNS, etc.), and familiarity with the Unix/Linux command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Students will use the Vega scanning tool, within a graphical Kali Linux environment, to test web services over the network and document vulnerabilities. Students will then use network packet capture tools such as Wireshark to verify their understanding of the vulnerabilities and testing procedures.
Basic web application knowledge (HTTP, URL parameters, etc.) and networking concepts (TCP/IP, DNS, etc.).
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Burp Suite is an industry standard suite of tools used by information security professionals for testing Web application security. Its tools work together to support the entire testing process, from initial mapping and analysis of an application's attack surface, through to finding and exploiting security vulnerabilities.
Students learn to use Burp tools to find security vulnerabilities in a web application. They will discover the application is vulnerable to cross-site scripting (XSS) attacks and will learn how to exploit the vulnerability to steal user credentials.
Basic web application knowledge (HTTP, URL parameters, etc.).
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Students will learn how to detect and exploit SQL injection vulnerabilities. By using several SQL injections techniques students will gather information about a remote database such as server operating system, database type, table names, and most importantly, table content. Students will then use sqlmap, a tool for SQL injection, to automate this process.
Basic knowledge of SQL database queries and familiarity with the Unix/Linux command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Web site reconnaissance is about gathering information about a web site. Of course, there is information published on the website that is intended for people to see. Then there is information such as the name and version of the software used in the website and information about databases used by web applications on the site. This is information the website owner may not want known but can be discovered using techniques covered by CYRIN labs in the Network Monitoring and Recon and Web Application Security Analysis categories.
In this lab students will learn to find additional information from documents on the website. These documents have associated with them document metadata, which is information attached to a file that isn't visible when the document is viewed. For example, metadata associated with a Microsoft Word document includes its creation time and the name of the person who created it. This is very likely information not intended to be publicly available.
Basic web application knowledge (HTTP, URL parameters, etc.) and familiarity with the Windows command prompt.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

This lab teaches three different Denial of Service attacks and techniques to mitigate them:
Basic web application knowledge (HTTP, URL parameters, etc.), networking concepts (TCP/IP, DNS, etc.), and familiarity with the Unix/Linux command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Where do you begin in network traffic analysis? Learn the process for examining a live or pre-recorded packet capture file using graphical tools such as Wireshark. Is there malicious activity? Learn to think like an attacker, going through the same methods the attacker would, to assess whether what you're seeing is "normal" or signs of an attack. At the same time, students will run basic network scans using nmap, while seeing how they appear in Wireshark. Finally, students will analyze packet traces indicative of HTTP-based attacks.
Basic familiarity with TCP/IP networking (advanced knowledge not required) and familiarity with the Unix/Linux command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Build on what you learned in Protocol Analysis I, this time using command line tools and techniques. You will use the ubiquitous tcpdump program, starting with simple capture tasks and then building up to complex filtering and display options. In the process, you will dig deeply into TCP and IP header fields, learning how these can be used to find the traffic you're interested in. You will examine ICMP, SSH, and HTTP traffic, including that from web shells commonly used in attacks. With the techniques learned in this exercise, you will be able to gather and filter packet capture data from server systems, then later process it on graphical security operations workstations.
The Protocol Analysis I lab or equivalent knowledge of Wireshark and TCP/IP packet capture. Familiarity with how to use the command line in Linux/Unix systems.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Students will learn to use the Cuckoo sandbox to determine if an executable or document is potential malware. If the executable is packed (compressed), they will learn to use a debugger to unpack it.
Basic knowledge of computer architecture and assembly language, and familiarity with the Unix/Linux command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Examine packet captures from actual intrusions and dive deeper into how attackers operate! Students will learn the details of protocols such as SMB and SSH by examining network traffic captures in Wireshark®, then will proceed to build network packets "by hand" in order to tunnel secret data in normal-looking traffic. Finally, students will learn the details of "web shell" payloads commonly used by attackers.
Detailed knowledge of networking protocols, including TCP/IP, DNS, and HTTP. Familiarity with Wireshark and the Unix/Linux command line.
The CYRIN Packet Capture Analysis and Manipulation exercise is recommended before starting this exercise.
3 hours, self-paced. Pause and continue at any time.
3 CPEs awarded on successful completion.

Get valuable experience extracting data from network packet captures! Students will use Wireshark® to analyze network packet traces containing normal network traffic and active attacks. Detailed information will be extracted from the traces by examining packets and by using Wireshark's built-in analysis and PCAP-manipulation tools.
Knowledge of the internals of networking protocols, including TCP/IP, DNS, and HTTP. Familiarity with Wireshark and the Unix/Linux command line.
The CYRIN Protocol Analysis labs will help you meet these prerequisites.
3 hours, self-paced. Pause and continue at any time.
3 CPEs awarded on successful completion.

Continue your exploration into malware's behavior on the network! Students will analyze network captures containing real, malicious network traffic, both by hand and using tools such as Security Onion and Sguil. Both malware spreading methods and command and control operations will be explored. In addition, students will create web shell payloads of their own to see how they operate from the inside.
Detailed knowledge of networking protocols, including TCP/IP, DNS, and HTTP. Familiarity with Wireshark and the Unix/Linux command line.
The CYRIN Intrusion Analysis using Network Traffic exercise is recommended before starting this exercise.
3 hours, self-paced. Pause and continue at any time.
3 CPEs awarded on successful completion.

Disk-based analysis is the cornerstone of cyber forensics, whether it be to track what a suspect was doing or simply to recover accidentally deleted files. This lab introduces students to the process of imaging and forensically analyzing disks, including finding artifacts such as deleted files. The free Autopsy® forensic browser will be used in addition to command-line programs from the open-source Sleuth Kit® tool set.
In order to get the most out of this lab, you should be comfortable with cyber forensics best practices (chain of evidence, etc.) and be comfortable with a Linux/Unix command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

GRR Rapid Response is an open source live forensics tool originally created by Google. GRR allows an investigator to collect data about running systems on a network, anywhere from one system to thousands. In this lab, students will perform live remote forensic investigations against running systems. Without having to take the systems offline for imaging, students will examine running processes and network connections, files and disk artifacts, and registry keys across multiple target machines in a forensically-sound manner.
You should have a basic familiarity with computer forensics processes and tools in order to get the most out of this lab.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.
Introduces students to the process of investigating usage of peer-to-peer (P2P) file sharing services for trading illicit content. Students learn what artifacts of P2P file sharing usage are left on a suspect’s hard drive, as well as how to extract forensically-relevant information from the raw data. Students then use Architecture Technology Corporation’s P2P Marshal™ software in a hands-on practical, gathering evidence from provided forensic disk images using Microsoft Windows®.
A copy of the P2P Marshal software is available free of charge to anyone enrolled in this course.
Basic cyber forensics knowledge and best practices are recommended.
4 hours, self-paced. Pause and continue at any time.
4 CPEs awarded on successful completion.
Analyzing a suspect system "live", before disconnecting it and imaging the disks, often yields valuable forensic evidence. Further, it can help you determine whether a crime has been committed at all, or whether the system contains evidence at all, thereby avoiding time-consuming examination of irrelevant machines. The Volatility® framework is the dominant open-source memory analysis framework, examining RAM snapshots from a large variety of operating systems in multiple formats. This lab introduces students to the process of capturing a live RAM image and analyzing it using Volatility. Students will learn about several Volatility plugins for analyzing a Windows memory image, then analyze actual RAM images, including one with active malware, and view the results.
In order to get the most out of this lab, you should be familiar with cyber forensics best practices (chain of evidence, etc.) and be comfortable with a Linux/Unix command line.
This lab does not directly discuss the process of acquiring a RAM image. There are several free tools available on-line for this purpose.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.
Analyzing a suspect system "live", before disconnecting it and imaging the disks, often yields valuable forensic evidence. Further, it can help you determine whether a crime has been committed at all, or whether the system contains evidence at all, thereby avoiding time-consuming examination of irrelevant machines. Rekall is an advanced, open-source memory capture and analysis framework that has expanded to include a variety of live incident response tools. This lab introduces students to the Rekall framework, both for extracting evidence from memory images and for analyzing the current live state of the system. Students will learn about several Rekall tools, both on the command line and via the interactive console, for analyzing memory images. Students will then analyze several images of Windows systems with in-memory malware.
In order to get the most out of this lab, you should be familiar with cyber forensics best practices (chain of evidence, etc.) and be comfortable with a Linux/Unix command line. An understanding of operating systems concepts, such as processes and network connections, is also required.
While this lab makes use of Rekall's "live" mode, which generates a virtual RAM image on the fly, this lab does not directly discuss the process of acquiring a RAM image. There are several free tools available on-line for this purpose.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.
A security analyst will likely be asked some time in his or her career to conduct a forensic analysis of a Windows workstation or server. In this lab the student will learn about forensic artifacts commonly found on Windows computers. Forensic artifacts are traces of user activity left behind on a computer even after the user logs out or the computer is shut down.
In this lab, students will investigate a suspected data breach by an employee of an organization. They will be given a disk image of the employee's Windows workstation. They will learn where to look for forensic artifacts and the use of tools such as Autopsy®, Registry Editor, RegRipper, LECmd, JumpList Explorer, RecentFileCacheParser, PECmd, and ShellBags Explorer to extract information from these artifacts.
Basic cyber forensics knowledge and best practices are recommended, as is familiarity with the Windows command prompt.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.
This course builds on the Introduction to P2P Forensics in order to provide students with a deeper understanding of how to extract evidence from a suspect’s hard drive. Students learn detailed file formats used by popular P2P software and methods for extracting information by hand. The course concludes with a hands-on practical using Architecture Technology Corporation’s P2P Marshal™ and provided forensic disk images using Microsoft Windows®.
A copy of the P2P Marshal software is available free of charge to anyone enrolled in this course.
You should complete the Introduction to P2P Forensics course first in order to get the most of this exercise.
4 hours, self-paced. Pause and continue at any time.
4 CPEs awarded on successful completion.
This course provides a deep dive into the eMule peer-to-peer file sharing system and client software. Students will learn how eMule stores forensically-relevant data on disk. The course concludes with a hands-on practical using Architecture Technology Corporation’s P2P Marshal™ and provided forensic disk images using Microsoft Windows®.
A copy of the P2P Marshal software is available free of charge to anyone enrolled in this course.
You should complete the Introduction to P2P Forensics course first in order to get the most of this exercise. The Advanced P2P Forensics course is recommended as well.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.
Get experience conducting an internal investigation on a realistic corporate network.
You are a security officer for a shipping company whose trucks have repeatedly been hijacked by a criminal organization. The criminals appear to have advance information on the routes of the trucks, despite the company changing routes frequently. Company executives suspect someone within the company is leaking truck route information to the criminals. Students will have to determine who is leaking the information, how, and to whom.
Knowledge of cyber forensics concepts and tools, as well as centralized logging configuration and analysis. Knowledge of the Linux bash shell will help you out as well.
3 hours, self-paced. Pause and continue at any time.
3 CPEs awarded on successful completion.

The ability to read and write shell scripts is an essential skill for system administrators. They are used to automate frequently executed tasks, saving system administrators time and reducing the likelihood of mistakes. This lab is brought to you by the Rochester Institute of Technology Global Cybersecurity Institute.
In this lab students will learn to write a simple Bash script that automates the task of creating user accounts, adding accounts to a group, and creating a shared workspace for this group.
Students must have some familiarity with the Unix/Linux Terminal and shell commands. They must also know how to edit text files using nano, vi/vim, or emacs.
Students without these prerequisites should first complete the free Getting Started with CYRIN lab.
1 hour, self-paced. Pause and continue at any time.
1 CPE awarded on successful completion.

The Linux and Windows command lines are powerful tools that allow software developers, system administrators, and users to quickly and efficiently perform tasks, without the need for a graphical user interface (GUI). Command line interfaces eliminate the need for scrolling through and clicking on GUI tabs and dialogs. The ability to use the command line is essential for managing Linux servers that typically do not have graphical user interfaces.
This lab introduces the Windows Command Prompt and PowerShell, and the Linux Terminal. It goes beyond the basics of the Windows PowerShell and Terminal covered by the Getting Started with CYRIN lab.
None.
1.5 hours, self-paced. Pause and continue at any time.
1.5 CPEs awarded on successful completion.

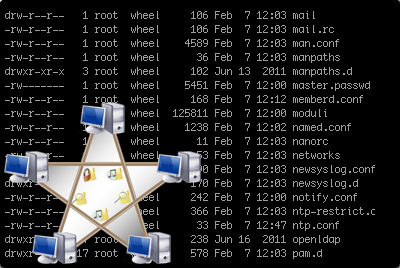
This lab teaches concepts that are fundamental to using and administering a system running the Linux operating system. The lab teaches the basics of the Linux file system and how to navigate it, the use of permissions on files and directories to manage access, command output redirection and pipes, and commands that will help an administrator be more efficient.
Knowledge of Linux is often essential for IT roles because it powers a significant portion of enterprise web and database servers, cloud infrastructures, and Internet of Things (IoT) devices.
The Getting Started with CYRIN lab.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

In this lab students will learn the fundamentals of Windows Operating System administration. They will use the Microsoft Management Console (MMC) for device and disk management, viewing events, managing users and user groups, and scheduling tasks. They will also learn about the Windows Registry and how to view and change registry settings. This lab is brought to you by Prof. David Hozza of Penn State University.
Basic familiarity with the Windows operating system.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

This lab will introduce students to MariaDB and MySQL by having them create a database, add tables to the database, populate data tables, and retrieve information from the database. They will do this using the MySQL command line interface. This lab is brought to you by the Rochester Institute of Technology Global Cybersecurity Institute.
MariaDB is a fork for the widely used MySQL database management system (DBMS). Both are open-source software and are largely compatible.
Basic understanding of relational databases. Some knowledge of SQL will be helpful but is not required.
1.5 hours, self-paced. Pause and continue at any time.
1.5 CPEs awarded on successful completion.

In this lab students will learn to use Jenkins, a widely used automation tool to set up a CI/CD (continuous integration/continuous delivery) pipeline. CI establishes a consistent and automated way to build, package, and test applications. CD automates the delivery of applications. A pipeline is the set of software integration, testing and deployment steps that the software being developed must go through. This lab is brought to you by the Rochester Institute of Technology Global Cybersecurity Institute.
CI/CD is the backbone of DevOps, a set of practices and tools that increases an organization’s ability to deliver applications and services at high speed, evolving and improving products at a faster pace.
Basic knowledge of web architecture, some familiarity with the Linux command line and text editors.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.
Active Directory (AD) is part of the Windows Domain Controller (DC). It is a service that stores information about users and network resources such as computers on the network. AD simplifies network management: Security policies can be defined on the AD and applied to all computers in the domain. User accounts can be created and managed centrally using the Active Directory Administrative Center. This lab is brought to you by the Rochester Institute of Technology-Global Cybersecurity Institute.
In this lab students will learn to install AD on a Windows DC, join computers to the domain, and create domain user accounts. After completing this lab, students are encouraged to do the CYRIN Using Active Directory to Manage Domain User Accounts lab, where they will learn to set up AD security policies and assign them to users and organizational units.
Some familiarity with the Windows operating system.
1.5 hours, self-paced. Pause and continue at any time.
1.5 CPEs awarded on successful completion.

Docker is a light-weight virtualization technology to package applications and their dependencies in a virtual container. Docker greatly simplifies software deployment because Docker containers can run on any Linux, Windows, or MacOS computer. Docker containers are isolated from one another and a single computer can run a very large number of containers. Knowledge of Docker is an essential for anybody involved with modern software development practices. This lab is brought to you by the Rochester Institute of Technology-Global Cybersecurity Institute.
In this lab students will learn basic Docker commands to pull container images from a registry, run them, change them, and push changes back to the registry. They will learn to use docker-compose to build an application consisting of multiple containers. Finally, they will learn the basics of Docker networking.
Some familiarity with the UNIX/Linux command line and with text editors. The free Getting Started with CYRIN labs covers these prerequisites.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

This lab introduces students to machine learning (ML) using neural networks. ML is a type of Artificial Intelligence (AI) that teaches computers to make decisions or predictions based on patterns they discover in large "training" datasets. Neural networks are the most common technology for machine learning. Students will learn how neural networks work by building, training, and evaluating a neural network to classify beers as IPAs or not-IPAs based on their bitterness and hoppiness ratings from a publicly available dataset of over a million BeerAdvocate® reviews.
Tools used in this lab include: (1) PyTorch, an open-source machine learning library for Python, and (2) Jupyter, an interactive document that provides an environment for prototyping and explaining code, and for exploring and visualizing data. Both PyTorch and Jupyter are used widely by the machine learning community.
Some familiarity with a programming language, preferably Python.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Students will learn the basics of cryptography, the science of encryption or the "hiding of information". Cryptography is the underpinnings of data security and privacy in the modern world. The lab begins with historical cryptographic techniques and progresses to modern digital cryptography. Topics covered include substitution codes, symmetric and asymmetric key cryptographic systems, and steganography (the hiding of messages in seemingly innocuous images, video, audio or text files). Applications of cryptographic techniques in blockchains, password security, and data integrity are also explored.
The Getting Started with CYRIN lab for a basic understanding of Linux and the Linux command line.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Buffer overflow is a software bug (vulnerability) that can be exploited by attackers to gain unauthorized access to systems. It is one of the best known software security vulnerabilities and still remains fairly common.
A buffer overflow happens when a program writes more data to a data structure, such as a string or array, than the memory allocated to that structure can hold. The data that does not fit into the structure "overflows" into surrounding memory and corrupts adjacent memory structures. An attacker can take advantage of this to insert and run malicious code.
Students will learn how memory is organized in a running program and then learn to craft an exploit that takes advantage of a buffer overflow bug in a vulnerable program. Successful exploitation of the vulnerability will give them root (super user) access to the system.
Students will also learn about programming practices that can reduce the likelihood of buffer overflow bugs, operating system protections the can make it harder for attackers to exploit such bugs, and ways in which these attacks can be detected.
Some familiarity with the Linux command line and file permissions.
Basic programming language concepts.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.
One of the most important skills in cyber defense is the ability to think like an attacker. How will an adversary break in to your systems? Are your sensitive files properly hidden from prying eyes? Can a dedicated attacker steal encryption keys that would allow them to impersonate you? Knowing how such attacks might work helps you securely configure and defend your systems.
Hone your skills and see how an attacker would exploit configuration weaknesses. This Capture the Flag (CTF) scenario lets you see first-hand an attacker's strategies for compromising your systems. Can you gain total control over a target system solely via a web application?
Familiarity with the UNIX
command line and
networking concepts, as well as knowledge of web
application vulnerabilities
(e.g., SQL injection). Hints are available if you get stuck!
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Build on your skills from the first Capture the Flag (CTF) scenario with a new web server setup—can you gain root access on this box? This CTF scenario lets you see first-hand how an attacker could go about compromising your systems.
Familiarity with the UNIX
command line and basic
networking concepts
(TCP/IP, DNS, etc), as well as knowledge of web
application vulnerabilities
(e.g., SQL injection). Hints are available if you get stuck!
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Test your skills against others as either an attacker attempting to compromise a system or a defender trying to prevent the attackers from doing damage. This is a head-to-head exercise, best played with two or more participants from your organization. Participants choose their own teams.
Knowledge of attack, pen-testing, and defensive techniques on Linux systems, including web application attacks, firewall configuration, etc. Familiarity with command-line tools on Linux systems (e.g., Metasploit).
Most importantly, be appropriately matched in skill with your opponent!
To get the most out of this exercise, you should complete the two Capture the Flag scenarios first.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

In this exercise, the student plays the role of a security admin of an enterprise network. They are asked to investigate a potential malware-based attack.
The student is told that an intrusion detection system has seen periodic outgoing connections from a computer within the enterprise network to a computer on the Internet. The student must block the outgoing traffic, determine the computer from which the traffic is originating, find the malware on that computer, examine it to see what information is being sent out, and stop the attack.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Students play the role of a network security administrator of an enterprise. They are told that a host on the Internet has been persistently scanning their network.
They will use an Incident Response Rack with intrusion detection systems and log analysis tools to determine:
Finally, they must block the attacker from the network.
After the attack is blocked, students will learn to exploit the vulnerability in the service.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

In this exercise the student is presented with an OT (Operational Technology) network that controls the HVAC system for a building. Malware in the network has forced the temperature in the building to uncomfortably low values.
The student is tasked with finding the source of the Modbus commands forcing the low temperatures: the computer originating the commands and the malware process on the computer. The malware might have hidden itself; the student must unhide the process and kill it.
The student should have some familiarity with: (1) The Linux operating system, including commands to view processes and network connections, (2) The pfSense firewall. Students without these prerequisites should consider completing the Linux Operating System Fundamentals for Systems Administrators and Firewall Configuration with pfSense labs before attempting this attack scenario.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Would you know if a device on your Operational Technology (OT) network was compromised on its way from the factory to you? Or if a contractor inadvertently installed some malware that didn't activate until months later?
This scenario presents just such an attack on the OT network—one of the existing devices on the network is intercepting and modifying SCADA traffic. It could be producing false measurements, or be sending commands to an unsuspecting device on behalf of the SCADA Server!
Incident response / forensic processes are required for this scenario. Familiarity with industrial control systems (ICS) network components and topologies will help as well.
1 hour, self-paced. Pause and continue at any time.
1 CPE awarded on successful completion.

It only takes one user clicking on a phishing e-mail to launch a devastating attack. Successful phishing attempts give an attacker access to your IT network resources, and possibly your OT network as well.
This scenario presents just such an attack—one of the users on the IT side of the network has inadvertently opened a malicious e-mail attachment. What are the consequences to the IT and OT networks, and how can this be contained and neutralized?
Incident response / forensic processes are required for this scenario. Familiarity with industrial control systems (ICS) network components and topologies will help as well.
1 hour, self-paced. Pause and continue at any time.
1 CPE awarded on successful completion.

A Denial of Service (DoS) attack can cripple your business operations, or do even worse to your physical infrastructure. How will you find and stop such an attack? How will your personnel perform when the system is in a degrated state?
This scenario presents just such an attack on the OT network—a DoS attack at the application layer, aimed at disrupting normal operations.
Incident response / forensic processes are required for this scenario. Familiarity with industrial control systems (ICS) network components and topologies will help as well.
1 hour, self-paced. Pause and continue at any time.
1 CPE awarded on successful completion.

A Denial of Service (DoS) attack can cripple your business operations, or do even worse to your physical infrastructure. How will you find and stop such an attack? How will your personnel perform when the system is in a degrated state?
This scenario presents just such an attack on the OT network—a DoS attack at the network layer, flooding your systems with bogus data and slowing operations to a crawl.
Incident response / forensic processes are required for this scenario. Familiarity with industrial control systems (ICS) network components and topologies will help as well.
1 hour, self-paced. Pause and continue at any time.
1 CPE awarded on successful completion.

Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.

Automatically-created CYRIN exercise in development.

Automatically-created CYRIN exercise in development.

Automatically-created CYRIN exercise in development.

Automatically-created CYRIN exercise in development.

Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
WorldSkills Ireland National Final 2023 Skill-54 Cybersecurity Module B

WorldSkills Ireland National Final 2023 Skill-54 Cybersecurity Module B Part 2. Part 1 is provided in a separate sheet.

WorldSkills Ireland National Final 2024 Skill-54 Cybersecurity Module A

Module C - CTF

Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.

In this lab, you will use the Windows and Linux clients to complete your objectives. You will be performing the following tasks:
Lab 7a (Identifying Security Vulnerabilities):
1. Demonstrate vulnerabilities.
2. Mitigate the vulnerability with Authentication.
Lab 7b (Securing the Storage Infrastructure):
1. Create network access entries.
2. Setup LDAP server.
3. Create groups and users on LDAP server.
4. Configure network access and group authentication for NFS.
5. Configure network access and group authentication for SMB/CIFS.
6. Create LUN masking.
In this lab, you will use the Windows and Linux clients to complete your objectives. You will be performing the following tasks:
1. Backup Openfiler configuration.
2. Backup LDAP configuration.
3. Create quota on SMB/CIFS share.
4. Repair failed RAID array.
Automatically-created CYRIN exercise in development.
In this lab, you will use the Windows and Linux clients to complete your objectives.
You will be performing the following tasks:
1. Demonstrate CIFS snapshot capabilities.
2. Demonstrate NFS snapshot capabilities.
3. Demonstrate iSCSI snapshot capabilities.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.

Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
In this lab, you will use the Windows client to complete your objectives. You will be performing the following tasks:
1. Create RAID partitions
2. Configure RAID 0
3. Configure RAID 1
4. Configure RAID 5 with Hot Spare
5. Configure RAID 10
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.

Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.

Automatically-created CYRIN exercise in development.

Automatically-created CYRIN exercise in development.

Automatically-created CYRIN exercise in development.

Automatically-created CYRIN exercise in development.

Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.

Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.

Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.

Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Cyber Range skills development environment for students taking the Cyber SKills module: Log Files and Event Analysis
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.

Automatically-created CYRIN exercise in development.
This scenario presents an attack from the IT network to the OT network. The attack starts approximately 5 minutes after the exercise begins. Use the initial 5 minutes to understand pre-attack conditions. Your task is to determine the nature of the attack, find its source, and neutralize it.

Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
MTU Cork CyberSec Soc Training Exercises
4 hours, self-paced. Pause and continue at any time.
4 CPEs awarded on successful completion.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
Automatically-created CYRIN exercise in development.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.
Automatically-created CYRIN exercise in development.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.
Automatically-created CYRIN exercise in development.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.
Automatically-created CYRIN exercise in development.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.
Automatically-created CYRIN exercise in development.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.

Automatically-created CYRIN exercise in development.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.
Automatically-created CYRIN exercise in development.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.
Automatically-created CYRIN exercise in development.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.
Automatically-created CYRIN exercise in development.
2 hours, self-paced. Pause and continue at any time.
2 CPEs awarded on successful completion.
Automatically-created CYRIN exercise in development.

Among the innovations built into the Cyber Skills Cyber Range are live exercises where students learn by doing.
Put your employees and students into an attacker’s mind by pitting teams against one another, launching and defending against a variety of realistic attacks. Help them build technical experience with exercises such as setting up web proxies, performing active scans, and discovering server vulnerabilities.

Unlike other training systems, the Cyber Skills Range allows for fast and easy creation of customized exercises. Exercise Builder allows for real-time modifications and updates that allow you to create labs and exercises to meet your specific training and system needs.
Progress is evaluated in real-time instead of conventional post-training evaluations and can be managed by your company’s CIO, CSO, or Head of IT. Educators love its real-world fidelity and automated student progress metrics. See where your students stumble in real-world scenarios, so you know exactly where more training is required. We call this Automated Performance Monitoring.

You’ve been hacked, or you only suspect you’ve been hacked. Now what?
View This CategoryOnce your network is set up securely, you must continue to be vigilant.
View This CategoryAs an IT administrator, it’s important to be aware of the tools potential adversaries are likely to use against your networks and your applications.
View This CategoryWeb-based applications are the most significant security exposure your organization faces.
View This CategorySetting up your network securely is the first step in preventing attacks and misuse of your resources.
View This CategoryDefense-in-depth requires individual network hosts to be set up securely, whether they be individual workstations, server systems, or cloud computing nodes.
View This CategorySecurely configuring web server software and frameworks is the foundation of creating secure web-based services.
View This CategoryGain insight that addresses trends, challenges, and best practices for defending Industrial Control Systems and SCADA networks.
View This CategoryTest your abilities with virtual capture-the-flag, defacement, forensics, and denial of service scenarios.
View This Category